Tools
Some things I’ve made. A collection of links scattered throughout blog posts.
Kali on GCP
DevOps for material for my information security management class. Includes a pen test lab on GCP. ( source code, how to use it )
NIST Cybersecurity Framework ⭤ 800‑53 Controls Mapping
The NIST CSF Core maps controls from 800-53 (and other) informative references, but only by code, which makes text-searching impossible. Mashup! ( website, source code )
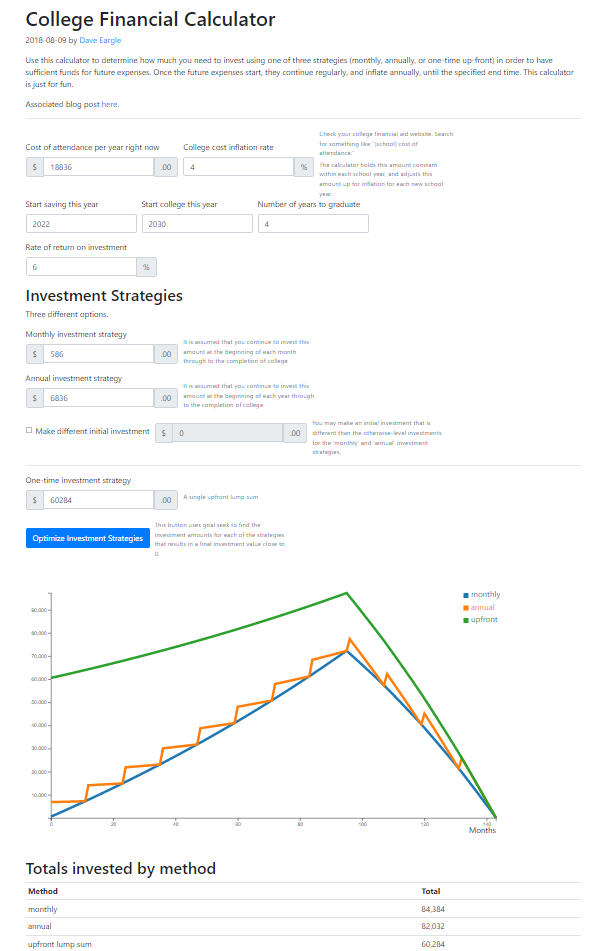
College Financial Calculator
Calculator that helps plan how much needs to be invested now, using a variety of investment strategies, in order to pay for college in the future. ( website, source code )
Ebscohost Query Maker
Tool to assist in making ebscohost Business Source Complete database queries of terms appearing in title-abstract-keywords of articles in top b-school journals. ( website, source code )
Grade curve calculator
Some schools have guidelines for distribution of letter grades for a class. This tool helps with compliance with those guidelines. ( website, source code )
Academic Research
I do academic research on things like the following:
- Behavioral Cybersecurity
- Political biases in Online News Consumption
- Identifying the informaiton systems research Nomological Network via Machine learning
- Using crowdsourcing platforms for research data collection
Learn more on my research page.
Open-source Contribution Curation
Check me out on github! deargle
I am involved more heavily with development of a few open-source repositories, such as the ones below.
Security-Assignments.com -- Content for an information security management course
Security-Assignments.com is a collection of course material that Tony Vance and I created and maintain for a course we have taught at various universities. Other professors at various universities are also using the material.
Students use Kali-on-GCP to complete the labs. This is a version of Kali that I customize to integrate with Google’s cloud platform services, including to be able to use SSH-in-the-browser and to log in via a google account. I build it using Packer and Vagrant. It uses nested virtualization. See the following repos:
- lab source code
-
kali-on-gcp source code
- Also see the Kali Pentest Lab!
- A GCP terraform-chef-vagrant-ansible c-c-combo infrastructure for creating pop-the-box networks
- Vagrant libvirt boxes for use on Kali-on-GCP (and elsewhere!):
psiTurk: An open platform for science on Amazon Mechanical Turk
Psiturk is a python Flask app bundled with a javascript library to facilitate interacting with mturkers through all stages of the AMT process – posting HITs, serving an experiment website, approving work, analyzing data.
I have been a core developer for psiTurk since during my phd in ~2016, and the lead developer since ~2018. I have done work on the psiturk command-line shell, a web interface, python unit testing, database optimizations, and bug fixes and features-adds throughout the python code.
- Citation
- Eargle, David, Gureckis, Todd, Rich, Alexander S., McDonnell, John, & Martin, Jay B. (2020, January 6). psiTurk: An open platform for science on Amazon Mechanical Turk (Version v2.3.7). Zenodo. http://doi.org/10.5281/zenodo.3598652
( source code, docs, paper )
Kepler Mapper: A flexible Python implementation of the Mapper algorithm
Kepler-mapper is a library implementing the Mapper algorithm in Python. KeplerMapper can be used for visualization of high-dimensional data and 3D point cloud data. KeplerMapper can make use of Scikit-Learn API compatible cluster and scaling algorithms.
KeplerMapper employs approaches based on the MAPPER algorithm (Singh et al.) as first described in the paper “Topological Methods for the Analysis of High Dimensional Data Sets and 3D Object Recognition”.
I became a core developer for this project circa 2018. I do work both on the python side and also the javascript / html d3 visualization side.
( Source code, docs, paper )
- My contributions
- I’m especially proud of these visualization features
- JOSS citation
- Hendrik van Veen, Nathaniel Saul, David Eargle, and Sam Mangham. “Kepler Mapper: A Flexible Python Implementation of the Mapper Algorithm.” Journal of Open Source Software 4, no. 42 (2019): 1315.
- Zenodo citation
- Hendrik Jacob van Veen, Nathaniel Saul, David Eargle, & Sam W. Mangham. (2019, October 14). Kepler Mapper: A flexible Python implementation of the Mapper algorithm (Version 1.4.1). Zenodo. http://doi.org/10.5281/zenodo.4077395
Random Curated Contributions
Some of my most cherished random contributions:
-
rapid7/metasploitable3, doing random stuff on the vagrant/chef side for the ubuntu image -
thc-hydra/thc-hydra, somehow I fixed an ssh bug, despite not knowing any C
-
angristan/openvpn-install, I fixed anip_forward=1bug -
benbalter/retlab(a jekyll theme), mild irony when I open PRs on a Github Exec’s Github Repos
Also, I publish a lot of my class content online. For example:
- security-analytics-assignments (website, source-code)
- business-analytics (website, source-code)
- security-assignments (website, source-code)